
AWS Identity and Access Management (IAM) policies are fundamental to securing your AWS infrastructure. In this comprehensive guide, we’ll explore everything from basic concepts to advanced implementations.
Understanding the Basics
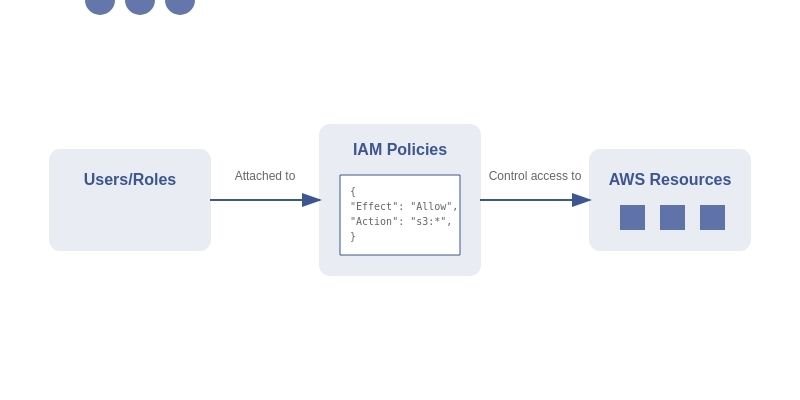
What are IAM Policies?
IAM policies are JSON documents that define permissions in AWS environments. Think of them as security guards that control who can access what resources and what actions they can perform with those resources.
Core Components
Every IAM policy contains three essential elements:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::my-bucket/*"
}
]
}Policy Structure Deep Dive
JSON Format Explained
Each policy must include a Version key (typically “2012-10-17”) and a Statement array. Statements are the heart of your policy, containing the actual permissions.
Essential Elements
- Effect: Either “Allow” or “Deny” – Deny always takes precedence
- Action: The operation you’re controlling (e.g., “s3:GetObject”)
- Resource: The AWS resource identifier (ARN) the action applies to
- Principal (optional): Who the policy applies to (used in resource-based policies)
Policy Types
- Identity-based Policies: Attached to users, groups, or roles
- Resource-based Policies: Attached to resources themselves
- Service Control Policies (SCPs): Organization-wide controls
Advanced Features
Condition Operators
Control when policies take effect:
{
"Condition": {
"IpAddress": {
"aws:SourceIp": ["192.0.2.0/24"]
}
}
}Policy Variables
Make policies dynamic:
{
"Resource": ["arn:aws:s3:::${aws:username}/*"]
}Tag-based Access Control
Manage permissions using resource tags:
{
"Condition": {
"StringEquals": {
"aws:ResourceTag/Environment": "Production"
}
}
}Best Practices
Security Guidelines
- Follow least privilege principle
- Avoid using wildcards (*) when possible
- Use explicit denies for critical resources
- Regularly audit permissions
Organizational Tips
- Use meaningful statement IDs (Sid)
- Group related permissions together
- Document complex conditions
- Maintain version control for policies
Implementation Strategies
- Start with minimum required permissions
- Use AWS managed policies as templates
- Implement policy boundaries for delegation
- Create reusable policy templates
Common Pitfalls and Solutions
Case Sensitivity Issues
- Actions are case-sensitive (“s3:GetObject” not “s3:getobject”)
- Effect values must be capitalized (“Allow” not “allow”)
- ARNs are case-sensitive for resource names
Wildcard Usage
- “*” matches zero or more characters
- “?” matches exactly one character
- Avoid using wildcards for sensitive operations
Service-Specific Requirements
- Some services require paired actions
- Not all services support resource-level permissions
- Cross-service permissions may need additional configuration
Testing and Validation
Policy Simulator Usage
- Test policies before applying them
- Simulate different scenarios
- Verify policy changes won’t break existing access
CloudTrail Integration
- Monitor policy usage patterns
- Track unauthorized access attempts
- Identify necessary permission adjustments
Access Analyzer Tips
- Enable AWS IAM Access Analyzer
- Review findings regularly
- Use suggestions to improve policies
- Monitor external access paths
Conclusion and Next Steps
Understanding and implementing IAM policies effectively is crucial for AWS security. Start with basic policies, test thoroughly, and gradually implement more advanced features as needed. Regular reviews and updates ensure your security posture remains strong.
Consider these next steps:
- Review your existing policies against these best practices
- Implement policy validation in your deployment pipeline
- Set up regular policy audits
- Stay updated with AWS security best practices
Remember: Good IAM policies balance security with usability. Take time to design them well, and they’ll serve as a robust foundation for your AWS security strategy.